$6 Trillion is the damage that will cost companies globally every year due to Cybercrime. Companies spend Billions of Dollars in Cyber security in order to keep their infrastructure and data secure to prevent an adversary from gaining access to a device or network and accessing sensitive information. Even then, hackers find ways, like brute-force techniques, to access sensitive data by compromising customer credentials. Irrespective of the security that is adapted on the server and network level, one of the biggest challenges, lies in protecting access to confidential information of individual customers, when they are accessing websites, mobile or software applications.
Millennials and elderly (above 50’s) remain the most vulnerable to cyber attacks as they are more prone to use simple passwords, access invitations from strangers on social platforms or open a scam email claiming to give them $2 Million that belonged to a business tycoon somewhere in an African country. Hackers try to deviate customer attention by creating lookalike websites and indirectly gaining access to confidential information. It becomes hard to identify the original website against a replica that looks the same except the domain name may vary with a single character (example: “l” instead of an “i” or double “e” instead of a single “e”) or names that matches your company name with a different domain extension. It will be surprising to know that their SEO will outperform yours and are listed on top of the search results. Unfortunately, your customer ends up on these platforms and share their credentials, assuming they are logging into their account. Firewalls or anti-spam applications won’t come handy in such situations.
So how do we protect such threats in the Cyber World?
Traditionally we all are accustomed to use one level of authentication, having a sophisticated password setup that cannot be guessed by machines or humans and securing applications using high level of encryption. Security experts have tried to enhance the security of customer authentication by adapting strict requirements like length of password, special characters, password expiry and much more. At the end of the day, a ‘one level password’ only system is still vulnerable due to the fact that customers may use the same password across multiple systems, or as explained earlier, unknowingly revealing their passwords, or the systems being compromised. These are very common and hard to protect from happening.
The best and proven method of data protection at customer level is by using Two Factor Authentication (2FA or TFA), also known as Multi Factor Authentication. 2FA involves the process of identifying a user to your system using two unique ways of authentication process, before they are given access to the platform or their personal information. A common example of 2FA in our day to day life is using ATM card for withdrawing money. It uses the ATM card as the first level of authentication and the PIN as the second level of authentication.
Two Factor Authentication increases the security of both your system and customer information as even if the password is compromised, the second level of authentication that is required is unknown and requires access to this authentication to further proceed. Despite having the inconvenience of a longer login process, we recommend enabling 2FA wherever possible: e-commerce sites, email accounts, social media applications, financial services, blogging platforms, accessing your secure servers and more.
An example of Two Factor Authentication is when using your Gmail account, where you are required to authenticate yourself using a PIN that is send to your mobile phone once you enter your user name and password. Google has implemented 2FA when the user is logging in to a device for the first time or when it is suspicious of any misuse.
Two Factor Authentication is implemented using any of the two information that a customer can provide – something they already know (password), they already have (physical device) or they are (biometric).

Something you know, you have and you are!
To implement 2FA, we rely on two information that the customer has to provide that is already available with them.
- Something you know: this is what the customer already knows in order to access the system, which is a password or a PIN that was set when creating the account
- Something you have: this is what the customer possesses and has access to – a physical device. This could be a mobile phone, hardware token generator or a software application that generates One Time Passwords (OTP)
- Something you are: a biologically unique feature of the customer (biometric information) like Fingerprint, Voice or Retina. This method is only possible when using hardware devices that can read the biometric details in real-time
As most of the existing systems use a password (something you know) as the first factor for authentication, adding an extra layer of protection (2FA) is possible by considering the use of OTP (something you have) or biometric (something you are).
- SMS (Short Message Service) to send OTP
- Emails to send OTP
- Mobile apps
- Voice calls to narrate OTP
- Physical one-time PIN (OTP) tokens
- Biometric Verification

In all these scenarios, it is important that we use Adaptive Context-Aware method in implementing 2FA to avoid inconvenience to users when they are regularly using your platform. Adaptive Context-Aware approach allows you to limit the 2nd layer of authentication based on a combination of below factors:
- Geographic location
- Devices being used
- Day and time
- IP addresses
- Browsers
SMS and Voice based OTP
One of the most commonly used for two factor authentications, this method utilizes what the customer already has (Mobile phone or Email) to send One Time Password (OTP) that is generated by the system at the time of registration or login. Once the user tries to login using their user name and password, an additional layer of security is initiated by sending a random generated 4 to 6 digit long PIN to their mobile phone as an SMS and/or a real time Voice call narrating the PIN. Customer has to enter this PIN (OTP) to gain further access to the system. If hackers can get hold of your password, they will not have access to your phone to obtain the PIN.
| Advantages | Disadvantages |
|---|---|
|
|
Email based OTP
This method is also commonly used and is similar to SMS OTP, except that the PIN generated can be longer and alphanumeric or the email can contain a unique and encrypted link which the user has to click to gain access. Emails are less used compared to SMS as it is not device dependent and the chances of the user using the same password for emails are highly likely.
| Advantages | Disadvantages |
|---|---|
|
|
Mobile App Based Tokens
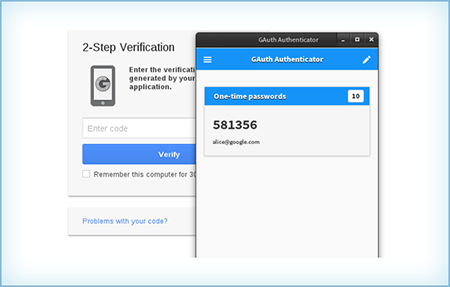
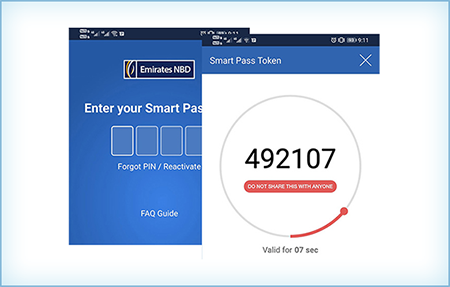
| Advantages | Disadvantages |
|---|---|
|
|
Biometric Verification
This two- factor authentication method uses biometrics, such as a fingerprint or iris scan, as a second factor. When a customer authenticates, they provide a passphrase along with their biometric data, the authentication service verifies both the passphrase and the biometric data with those provided at enrolment, and grants or denies access to resources. Biometric verification can only be used on mobile applications and devices that support biometric reading. It is important to use high-security encryption method while biometric data is hashed and stored in the back end system.
| Advantages | Disadvantages |
|---|---|
|
|
Physical One Time Pin Tokens
This authentication method uses a hardware token device that displays tokens that are frequently changed. This method is popularly used in enterprise systems and banks. Synchronization of the hardware generated token to the backend system is very critical in this method. Physical tokens work in the same way as that of Mobile App (software) based tokens, except the fact that here a physical device (like a Dongle) is used.
| Advantages | Disadvantages |
|---|---|
|
|
Validity of OTP or Tokens
It is important that the validity of OTP or Token is set to the minimal time possible to avoid it being compromised. If the transaction is of financial in nature, it is recommended to limit the expiry to a maximum of 2 minutes. If the access is only for general account details, the expiry can be set up to a maximum of 5 minutes.
Once the token is generated it is important to showcase the expiry details and provide a count down so that the customer checks the relevant information and enters the details on the screen. The customer should also have the option to regenerate the OTP or Token if they were not able to receive it initially. Retrial for sending a new OTP or Token as well as the customer trying different values need to be limited (maximum 5 times) and in case the limit is exceeded, you can disable access to their account for a period of time and inform them via other communication channels.
Any continuous attempt on entering the OTP or Tokens should be tracked and proper measures should be implemented to block the account and inform the customer.
Solutions for 2FA
Two Factor Authentication implementations are fairly easy when using SMS or Email based OTP, provided you are only to generate a random OTP and verify it against user entry. If we are to have a robust and more secure 2FA platform, it is advisable to opt for a ready to use platform from industry experts who have SMS, Email and Voice solutions. Depending on the solution opted for, a simple layer of SDK integration is what will be required from your team. These solutions will also cover various aspects of user verification and other criteria mentioned earlier.
“Companies spend millions of dollars on firewalls and secure access devices, and it’s money wasted because none of these measures address the weakest link in the security chain: the people who use, administer and operate computer systems” – Kevin Mitnick
It’s no longer a question of should Two Factor Authentication be implemented, but rather when. Speak to our security experts to analyze your website, mobile application or software application and recommend the most suitable 2FA solution.



